Purpose of this articles giving idea what automation solution you can offer from my developed use case so far.
VRA as any other products in the market keep evolving, so whatever seems so difficult to automate in the past might became very easy to accomplish in current or future state.
This diagram shown developed use cases.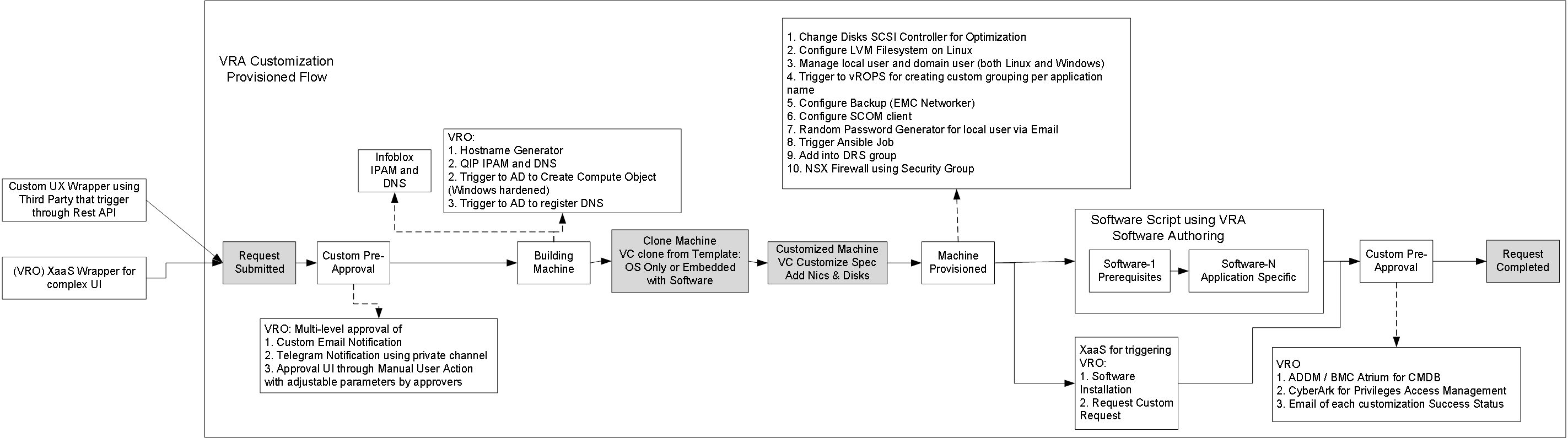
VRA Lifecycle
Here’s some descriptions of automation process on VRA
Request Submitted
Two options for triggering VRA request
- Using VRO to trigger VRA request, and then make user interface using VRO presentation. This method usually called XaaS Wrapper.
- Using third party or even build your own user interface and then trigger the VRA API or even you can trigger VRO API that already being wrapped and simplified.
Pre-Approval States
Normally out of the box pre-approval is already enough for most of the use cases. Here’s some use case that might require using external approval as trigger:
- Integration with third party solutions for approval mechanism –> personally I haven’t got chance to test or receive any project request for this use case.
- Ability to modify input parameters. We can leverage Manual User Actions as method of approving the request.
Post-Approval States
Deployment Post approval states is the last states before releasing deployment to the requestor. So if we have software authoring as part of the solutions, then the step that possible for triggering automation is during post-approval states.
Here’s some use case that might require automation triggered after software authoring states:
- Trigger third party application only after software successfully triggered
- Checklist email for all customization request
Grouping of the use case:
Notification method
- Email notification
- Telegram notification through private channel
IPAM & DNS
- Vital QIP
- Infoblox
Hostname Generator
- Using VRO as logic
- Third Party Application
Windows Active Directory
- Computer Object for OU Placement (either for hardening or object placement)
- Windows DNS
Virtual Machine Modification
- Utilize SCSI Controller for VM best practice
- Add into DRS group
User Management
- Create Windows/Linux Local User
- Generate Random Password and sent it to the requestor
- Assign privileges for the user (local or domain). Sudoers for Linux, grouping for Windows
Integration with VMware Solutions
- Create VROPS custom group and assign the policy
- NSX Firewall management
Common Use Case
- Filesystem creation (LVM)
Backup Software
- EMC Networker
Configuration Manager
- Ansible tower (AWX)
CMDB
- BMC Atrium (ADDM)
Privilage Access Management
- Cyberark Password Vault
Other Specific Use Case
- Windows SCOM
- Manual Service Request (refer to my blog for more information about manual service request)
- Checklist of automation status (success/failure)
Software Automation:
Here’s List of third-party software applications that has been automated. Also, combination of two tier or three tier applications
Web/App:
- Apache HTTPD on Linux and Windows
- Apache Tomcat on Linux and Windows
- IBM Web Server on Linux
- IBM WebSphere MQ on Linux
- IBM WAS on Linux
- IIS on Windows
- JBOSS EAP on Linux
- Oracle Weblogic on Windows
Database:
- DB2 on Linux
- SQL Server on Windows
- Oracle DB on Linux
- 2 nodes SQL Server Always on Availability Group on Windows
- 2 nodes Enterprise DB using EFM